A) The scan job is scheduled to run during off-peak hours.
B) The scan output lists SQL injection attack vectors.
C) The scan data identifies the use of privileged-user credentials.
D) The scan results identify the hostname and IP address.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Two users must encrypt and transmit large amounts of data between them. Which of the following should they use to encrypt and transmit the data?
A) Symmetric algorithm
B) Hash function
C) Digital signature
D) Obfuscation
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A company is implementing MFA for all applications that store sensitive data. The IT manager wants MFA to be non-disruptive and user friendly. Which of the following technologies should the IT manager use when implementing MFA?
A) Onetime passwords
B) Email tokens
C) Push notifications
D) Hardware authentication
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Corporations choose to exceed regulatory framework standards because of which of the following incentives?
A) It improves the legal defensibility of the company.
B) It gives a social defense that the company is not violating customer privacy laws.
C) It proves to investors that the company takes APT cyber actors seriously
D) It results in overall industrial security standards being raised voluntarily.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following attackers generally possesses minimal technical knowledge to perform advanced attacks and uses widely available tools as well as publicly available information?
A) Hacktivist
B) White hat hacker
C) Script kiddle
D) Penetration tester
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An organization is developing its mobile device management policies and procedures and is concerned about vulnerabilities that are associated with sensitive data being saved to a mobile device, as well as weak authentication when using a PIN. As part of some discussions on the topic, several solutions are proposed. Which of the following controls, when required together, will address the protection of data-at-rest as well as strong authentication? (Choose two.)
A) Containerization
B) FDE
C) Remote wipe capability
D) MDM
E) MFA
F) OTA updates
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following can be used to increase the time needed to brute force a hashed password?
A) BCRYPT
B) ECDHE
C) Elliptic curve
D) Diffie-Hellman
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An analyst generates the following color-coded table shown in the exhibit to help explain the risk of potential incidents in the company. The vertical axis indicates the likelihood or an incident, while the horizontal axis indicates the impact. 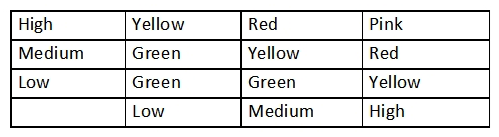 Which of the following is this table an example of?
Which of the following is this table an example of?
A) Internal threat assessment
B) Privacy impact assessment
C) Qualitative risk assessment
D) Supply chain assessment
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A company wants to implement a wireless network with the following requirements: All wireless users will have a unique credential. User certificates will not be required for authentication. The company's AAA infrastructure must be utilized. Local hosts should not store authentication tokens. Which of the following should be used in the design to meet the requirements?
A) EAP-TLS
B) WPS
C) PSK
D) PEAP
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network technician is setting up a new branch for a company. The users at the new branch will need to access resources securely as if they were at the main location. Which of the following networking concepts would BEST accomplish this?
A) Virtual network segmentation
B) Physical network segmentation
C) Site-to-site VPN
D) Out-of-band access
E) Logical VLANs
Correct Answer

verified
Correct Answer
verified
Multiple Choice
As part of a new industry regulation, companies are required to utilize secure, standardized OS settings. A technical must ensure the OS settings are hardened. Which of the following is the BEST way to do this?
A) Use a vulnerability scanner.
B) Use a configuration compliance scanner.
C) Use a passive, in-line scanner.
D) Use a protocol analyzer.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
After a merger between two companies a security analyst has been asked to ensure that the organization's systems are secured against infiltration by any former employees that were terminated during the transition. Which of the following actions are MOST appropriate to harden applications against infiltration by former employees? (Select TWO)
A) Monitor VPN client access
B) Reduce failed login out settings
C) Develop and implement updated access control policies
D) Review and address invalid login attempts
E) Increase password complexity requirements
F) Assess and eliminate inactive accounts
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An administrator is replacing a wireless router. The configuration of the old wireless router was not documented before it stopped functioning. The equipment connecting to the wireless network uses older legacy equipment that was manufactured prior to the release of the 802.11i standard. Which of the following configuration options should the administrator select for the new wireless router?
A) WPA+CCMP
B) WPA2+CCMP
C) WPA+TKIP
D) WPA2+TKIP
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following refers to the term used to restore a system to its operational state?
A) MTBF
B) MTTR
C) RTO
D) RPO
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A security analyst is testing both Windows and Linux systems for unauthorized DNS zone transfers within a LAN on comptia.org from example.org. Which of the following commands should the security analyst use? (Select two.)
A) nslookup comptia.org set type=ANY ls-d example.org
B) set type=MX example.org
C) dig -axfr comptia.org@example.org
D) ipconfig/flushDNS
E) ifconfig eth0 down ifconfig eth0 up dhclient renew
F) dig@example.org comptia.org
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A company is determining where to host a hot site, and one of the locations being considered is in another country. Which of the following should be considered when evaluating this option?
A) Mean RTO
B) Mean RPO
C) Data sovereignty
D) Data destruction laws
E) Backup media recycling policies
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An administrator discovers the following log entry on a server: Nov 12 2013 00:23:45 httpd[2342]: GET /app2/prod/proc/process.php?input=change;cd%20../../../etc;cat%20shadow Which of the following attacks is being attempted?
A) Command injection
B) Password attack
C) Buffer overflow
D) Cross-site scripting
Correct Answer

verified
Correct Answer
verified
Multiple Choice
After a merger between two companies a security analyst has been asked to ensure that the organization's systems are secured against infiltration by any former employees that were terminated during the transition. Which of the following actions are MOST appropriate to harden applications against infiltration by former employees? (Choose two.)
A) Monitor VPN client access
B) Reduce failed login out settings
C) Develop and implement updated access control policies
D) Review and address invalid login attempts
E) Increase password complexity requirements
F) Assess and eliminate inactive accounts
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A security analyst notices anomalous activity coming from several workstations in the organizations. Upon identifying and containing the issue, which of the following should the security analyst do NEXT?
A) Document and lock the workstations in a secure area to establish chain of custody
B) Notify the IT department that the workstations are to be reimaged and the data restored for reuse
C) Notify the IT department that the workstations may be reconnected to the network for the users to continue working
D) Document findings and processes in the after-action and lessons learned report
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An organization requires three separate factors for authentication to sensitive systems. Which of the following would BEST satisfy the requirement?
A) Fingerprint, PIN, and mother's maiden name
B) One-time password sent to a smartphone, thumbprint, and home street address
C) Fingerprint, voice recognition, and password
D) Password, one-time password sent to a smartphone, and text message sent to a smartphone
Correct Answer

verified
Correct Answer
verified
Showing 141 - 160 of 1164
Related Exams