A) traffic policing
B) CB-WFQ
C) MDRR
D) WRED
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which two statements about QoS marking are true? (Choose two.)
A) Class-based marking occurs after packet classification
B) MPLS EXP and DSCP are Layer 2 marking fields
C) QoS marking establishes a trust boundary that scheduling tools later depend on
D) Shaping is one of the ways that packets can be remarked
E) 802.1Q/p CoS bits and IP Precedence are Layer 3 marking fields
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which two components are of effective change management planning? (Choose two.)
A) a change validation mechanism
B) a what-if analysis for each proposed change
C) a multi-discipline change management team
D) an automated change management tracking system
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which two benefits can be obtained by protecting the control plane of a network device? (Choose two.)
A) preserves the confidentiality of traffic encrypted by IPsec
B) prevents the delivery of packets from spoof sources
C) maintains routing protocol adjacencies with local neighbors
D) maintains remote management access to the router
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are deploying a nationwide intranet solution for a company with 4 data centers and 400 remote branches connected via a provider-based solution. As part of the network design, you must ensure efficient content distribution of training material to remote sites. Which VPN technology leverages replication in the network core and provides for efficient bandwidth optimization?
A) IPsec
B) GRE
C) VPLS
D) MPLS Layer 3 VPN
E) L2TPv3
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which two actions are performed at the distribution layer of the three-layer hierarchical network design model?
A) fault isolation
B) QoS classification and marking boundary
C) fast transport
D) reliability
E) redundancy and load balancing
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The Sender Policy Framework (SPF) is an open standard specifying a technical method to prevent sender address forgery. When configuring the SPF exponential backoff timer, which one of the following items is among the primary issues to consider?
A) number of external routes
B) area size
C) average SPF run time
D) interface stability
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. 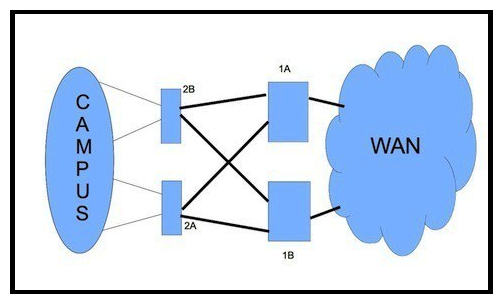 How would you redesign the network to improve availability of the routers 1A and 1B at the core site?
How would you redesign the network to improve availability of the routers 1A and 1B at the core site?
A) Enable Graceful Restart Helper for OSPF
B) Use link bundles over multiple slots
C) Use APS Ethernet circuits and redundant interfaces
D) Create a multichassis system with the two routers
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is a key design aspect to be considered when designing an IP network that will be carrying real-time VoIP traffic?
A) Minimizing total bidirectional end-to-end delay to 0-150 ms
B) Minimizing total unidirectional end-to-end delay to 150-500 ms
C) Minimizing total bidirectional end-to-end delay to 0-50 ms
D) Minimizing total unidirectional end-to-end delay to 0-150 ms "Pass Any Exam. Any Time." - www.actualtests.com 57 Cisco 352-001 Exam
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You work as a network technician, study the exhibit carefully. In an MPLS-enabled network, a service provider has three N-PEs and three U-PEs. The VPLS and H-VPLS services are MPLS-enabled. Two customers have subscribed to this Layer 2 service. In order to provide full connectivity between the customer sites, how many LDP sessions must be created between the PE devices? 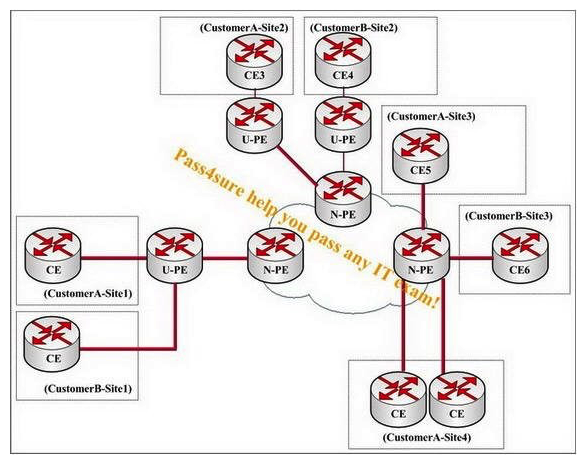
A) 4
B) 6
C) 10
D) 12
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are designing a solution to eliminate the risk of high CPU utilization on a core network composed of CRS-1 devices. Which option would eliminate the risk of high CPU utilization across the network?
A) Use Local Packet Transport Services (LPTS) to manage hardware SNMP flow rate.
B) Use the in-band control plane policy feature to reduce the SNMP flow rate.
C) Use the control plane policy feature and reduce SNMP flow rate.
D) Use control-plane management-plane in-band and reduce the SNMP flow rate.
E) Use the control-plane management-plane out-of-band feature to reduce the SNMP flow rate.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are a network technician for the P4S company, study the exhibit carefully. P4S-R1 is redistributing 10.1.5.0/24 into Area 1 in this network. Which LSA containing 10.1.5.0/24 will P4S-R6 have in its database? 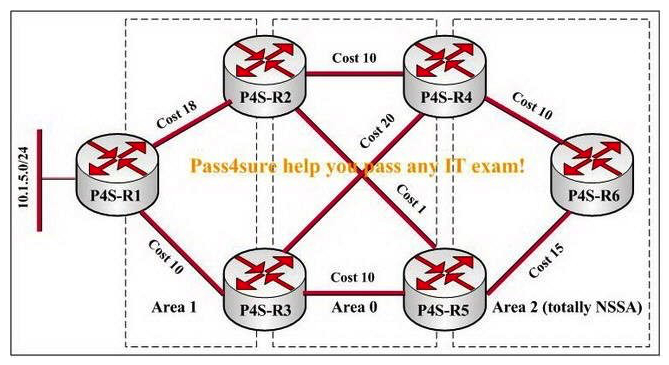
A) P4S-R6 will have a border router (type 4) LSA in its local database for 10.1.5.0/24.
B) P4S-R6 will have an NSSA external (type 7) LSA in its local database for 10.1.5.0/24.
C) P4S-R6 will have an external (type 5) LSA for 10.1.5.0/24 in its local database.
D) P4S-R6 will not have any LSAs containing 10.1.5.0/24.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which design concern should be accounted for in all Layer 3 virtualization technologies?
A) Layer 3 redundancy
B) packet sizing
C) application usage
D) Layer 3 stability
Correct Answer

verified
Correct Answer
verified
Multiple Choice
As part of a new network design, you are helping the Network Management Team to develop a proactive report to identify places in the network where problems may happen. The network management tool can poll the network devices only via SNMP GET operations. Which two threshold- crossing metrics should you include in this report? (Choose two.)
A) packet loss
B) CPU utilization
C) heat dissipation
D) IP reachability
E) energy consumption
F) link bandwidth utilization
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Connecting four routers running IS-IS to a single Ethernet link. Then, a fifth router is connected, the priority of this router is higher than that of the other four. What will happen?
A) The new router will not be elected DIS unless the current DIS fails.
B) The new router will become the DIS without causing a temporary disruption in traffic through the link.
C) The new router will not be elected DIS unless it has the lowest NET ID.
D) The new router will become the DIS and cause a temporary disruption in traffic through the link.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Company X will be integrating an IPv6 application into their network and wants to develop a test environment to evaluate application performance across the network. This application will require both unicast and multicast communications. The company can do this implementation only in certain areas of its existing IPv4-only network, but wants all areas to communicate with each other. When developing the design to provide connectivity between these testing locations, what tunneling technology would work in this scenario?
A) ISATAP
B) 6to4
C) DMVPN
D) 6vPE
E) 6PE
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. "Pass Any Exam. Any Time." - www.actualtests.com 5 Cisco 352-001 Exam 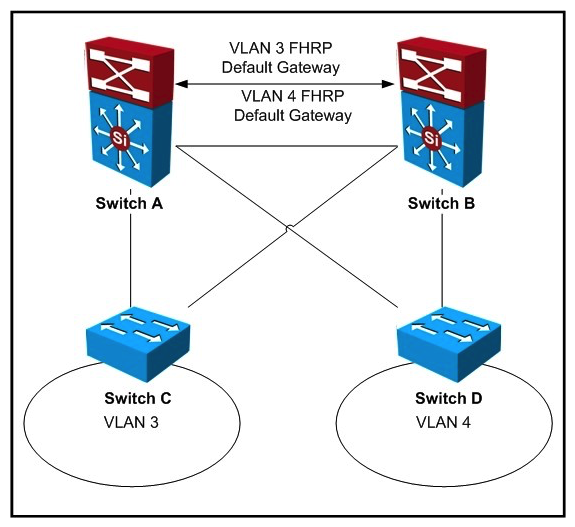 If IEEE 802.1w is in use for this network design, what are two locations where spanning-tree root can be placed to ensure the least-disruptive Layer 2 failover for clients within VLANs 3 and 4? (Choose two.)
If IEEE 802.1w is in use for this network design, what are two locations where spanning-tree root can be placed to ensure the least-disruptive Layer 2 failover for clients within VLANs 3 and 4? (Choose two.)
A) Switch A
B) Switch B
C) Switch C
D) Switch D
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which three processes are part of the ITILv3 Service Operation? (Choose three.)
A) service-level management
B) change management
C) incident management
D) problem management
E) release and deployment management
F) event management
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network designer decides to connect two labs together to test multicast features interoperability. Before the networks are connected together, the network administrator mentions that overlapping multicast IP addresses between the two labs will cause issues because all the routers on the network are provisioned for Source-Specific Multicast using IGMPv3. Which statement about the connectivity of both multicast domains is true?
A) IGMPv3 can support overlapping multicast IP addresses between the labs
B) IGMPv3 cannot support overlapping multicast IP addresses between the labs
C) IGMPv3 requires NAT to support the overlapping multicast IP addresses between the labs
D) IGMPv3 requires a unique RP when connecting both labs together
Correct Answer

verified
Correct Answer
verified
Multiple Choice
 Refer to the exhibit. Company A migrated from Frame Relay WAN to Metro-Ethernet E-LAN service. Router B and C have only eBGP neighbor adjacency with router A using their Metro-Ethernet IP addresses. What happens when host E sends a packet to host F?
Refer to the exhibit. Company A migrated from Frame Relay WAN to Metro-Ethernet E-LAN service. Router B and C have only eBGP neighbor adjacency with router A using their Metro-Ethernet IP addresses. What happens when host E sends a packet to host F?
A) Packet goes from router B to A and C
B) Packet is dropped by router B.
C) Packet goes from router B to C
D) Packet goes from router B to Aand is dropped by router A due to the split-horizon rule.
Correct Answer

verified
Correct Answer
verified
Showing 21 - 40 of 660
Related Exams