Correct Answer

verified
Correct Answer
verified
Multiple Choice
_____ is an authenticating server for EAP.
A) IAS
B) IIS
C) ISA
D) RADIUS
Correct Answer

verified
Correct Answer
verified
Essay
List the six specific fields in the AH.
Correct Answer

verified
1. Next header
2. Payload leng...View Answer
Show Answer
Correct Answer
verified
2. Payload leng...
View Answer
True/False
In stream cipher, a specific key size is used for encryption.
Correct Answer

verified
Correct Answer
verified
Essay
List six applications that can be used with SSL.
Correct Answer

verified
1. E-commerce
2. HTT...View Answer
Show Answer
Correct Answer
verified
2. HTT...
View Answer
True/False
Was AES originally developed for the U.S. National Security Agency?
Correct Answer

verified
Correct Answer
verified
True/False
When a network consists of Windows 2000 or later operating systems, Kerberos is the preferred logon authentication method.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
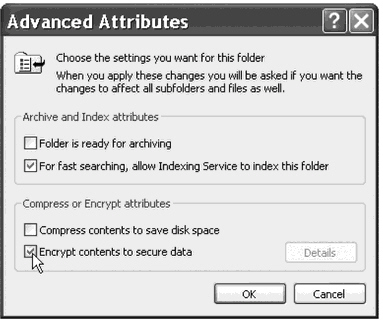 What form of encryption is being enabled in the figure above?
What form of encryption is being enabled in the figure above?
A) EFS
B) MPPE
C) DES
D) CFS
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following cipher command-line parameters copies encryption key and certificate data to a file that is encrypted for use by the cipher user?
A) /?
B) /k
C) /e
D) /x
Correct Answer

verified
Correct Answer
verified
Short Answer
____________________ is the science of creating secret messages.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
When following the ISO _____ format, a digital certificate includes a basic set of encrypted information.
A) X10
B) X.502
C) X.509
D) X 802.3
Correct Answer

verified
Correct Answer
verified
True/False
CFS can be used for remote file access through the NFS used by Netware systems.
Correct Answer

verified
Correct Answer
verified
Essay
List and provide the key lengths for the three different flavors of RSA used by MPPE.
Correct Answer

verified
1. Basic encryption, which use...View Answer
Show Answer
Correct Answer
verified
View Answer
Multiple Choice
Which authentication method is used on networks and in remote communications, typically employing Remote Authentication Dial-in User Servers and is compatible with many encryption methods?
A) SSL
B) Kerberos
C) EAP
D) TLS
Correct Answer

verified
Correct Answer
verified
Multiple Choice
When was the RSA encryption method created?
A) 1967
B) 1977
C) 1987
D) 1997
Correct Answer

verified
Correct Answer
verified
True/False
Today, Kerberos is the most commonly used form of security for communications and transactions over the Web.
Correct Answer

verified
Correct Answer
verified
True/False
Was SSH developed by Netscape to provide authentication security for TCP/IP applications such as FTP and Telnet?
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which version of hashing algorithm uses a mathematical formula to reduce a message to 160 bits and then hashes a digital signature to go with the message?
A) MD2
B) MD4
C) MD5
D) SHA-1
Correct Answer

verified
Correct Answer
verified
Essay
List five common types of attacks on encryption and authentication.
Correct Answer

verified
1. Brute force
2. Accessing pa...View Answer
Show Answer
Correct Answer
verified
2. Accessing pa...
View Answer
Multiple Choice
What does SSH use to authenticate a communications session that uses passwords?
A) Digital certificates
B) RSA
C) EAP
D) Both a and b
E) Both a and c
Correct Answer

verified
Correct Answer
verified
Showing 21 - 40 of 86
Related Exams